I'm running two ESXi servers but I'm not using vCenter because I find it to be too resource intensive. And to run my K8s host VM's I don't really need it.
Not running vCenter makes it somewhat more difficult to get certificates into the ESXi hosts. At least, all the examples I can find use too many unnecessary steps for my taste. So I set out to find the easiest way to get this done.
The first step is to make yourself a CA cert and private key. I'm using this openssl config file:
HOME = .
RANDFILE = $ENV::HOME/.rnd
####################################################################
[ ca ]
default_ca = CA_default # The default ca section
[ CA_default ]
default_days = 1000 # How long to certify for
default_crl_days = 30 # How long before next CRL
default_md = sha256 # Use public key default MD
preserve = no # Keep passed DN ordering
x509_extensions = ca_extensions # The extensions to add to the cert
email_in_dn = no # Don't concat the email in the DN
copy_extensions = copy # Required to copy SANs from CSR to cert
base_dir = .
certificate = $base_dir/cacert.pem # The CA certifcate
private_key = $base_dir/cakey.pem # The CA private key
new_certs_dir = $base_dir # Location for new certs after signing
database = $base_dir/index.txt # Database index file
serial = $base_dir/serial.txt # The current serial number
unique_subject = no # Set to 'no' to allow creation of
# several certificates with same subject.
####################################################################
[ signing_policy ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
####################################################################
[ signing_req ]
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer
basicConstraints = CA:FALSE
keyUsage = digitalSignature, keyEncipherment
####################################################################
[ req ]
default_bits = 4096
default_keyfile = cakey.pem
distinguished_name = ca_distinguished_name
x509_extensions = ca_extensions
string_mask = utf8only
####################################################################
[ ca_distinguished_name ]
countryName = NL
countryName_default = NL
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Flevoland
localityName = Almere
localityName_default = Almere
organizationName = Organization Name (eg, company)
organizationName_default = singel.home
organizationalUnitName = Organizational Unit (eg, division)
organizationalUnitName_default = singel.home
commonName = ca.singel.home
commonName_default = ca.singel.home
emailAddress = Email Address
emailAddress_default = flores@eken.nl
####################################################################
[ ca_extensions ]
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always, issuer
basicConstraints = critical, CA:true
keyUsage = keyCertSign, cRLSignSave this file as openssl-ca.cnf, and issue this command:
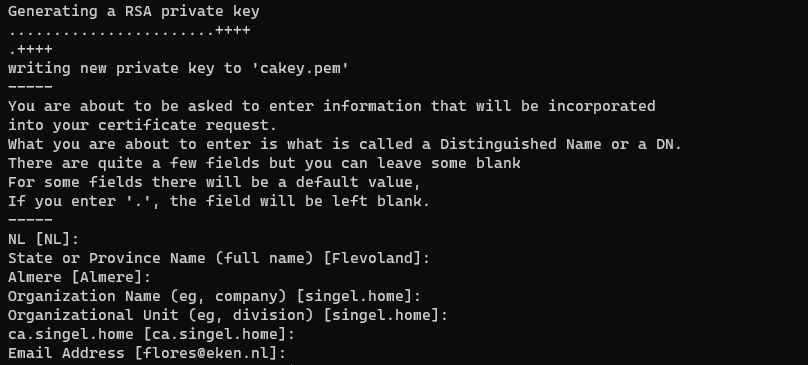
openssl req -x509 -config openssl-ca.cnf -newkey rsa:4096 -sha256 -nodes -out cacert.pem -outform PEM -days 3000
Output should be something like:
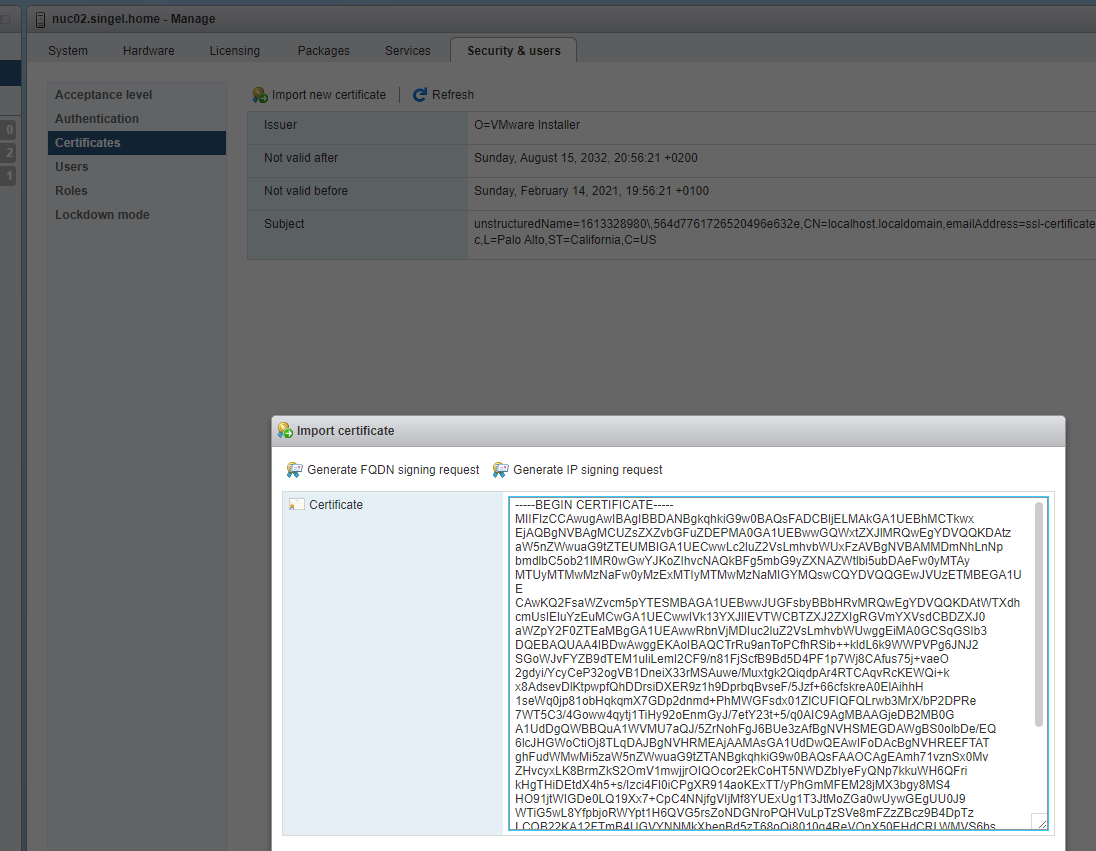
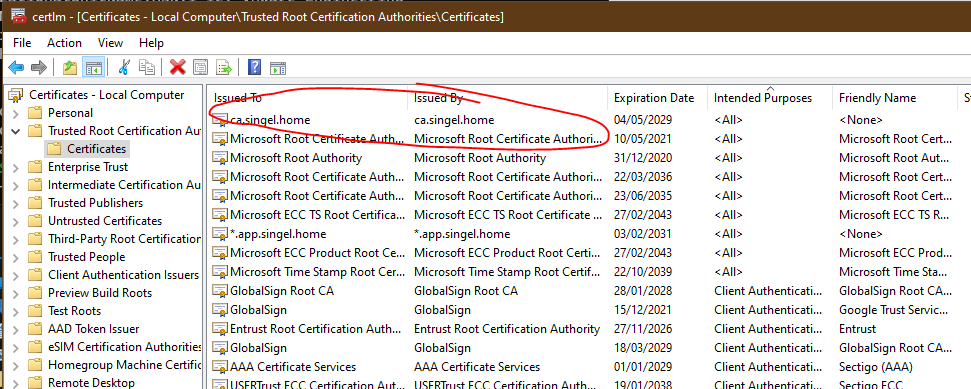
This will give you two files: cacert.pem and cakey.pem with this our CA is done. To make the certificates you will issue valid, you import the cacert.pem certificate as Trusted Root Certification Authority:
Before we can sign CSR's we need to additional files, to create those I used:
$ touch index.txt
$ echo '01' > serial.txtNow, to create a certificate for ESXi the easiest way is to use the UI to get the CSR here:
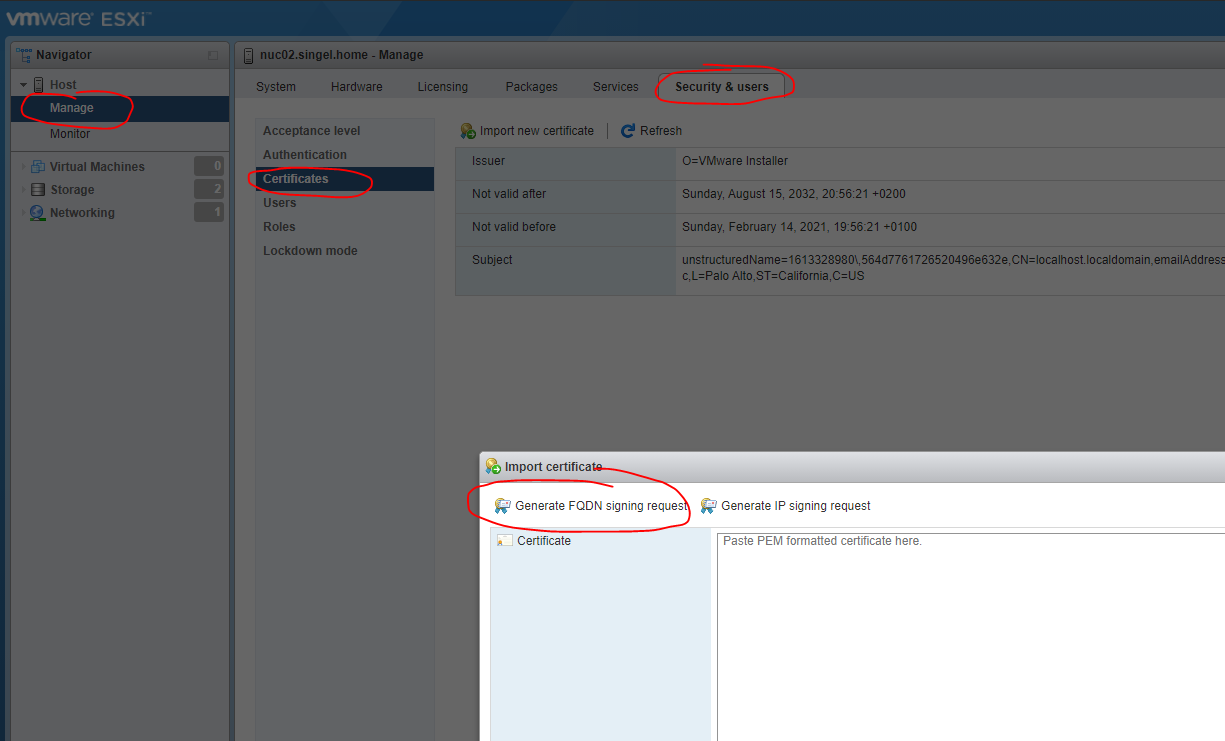
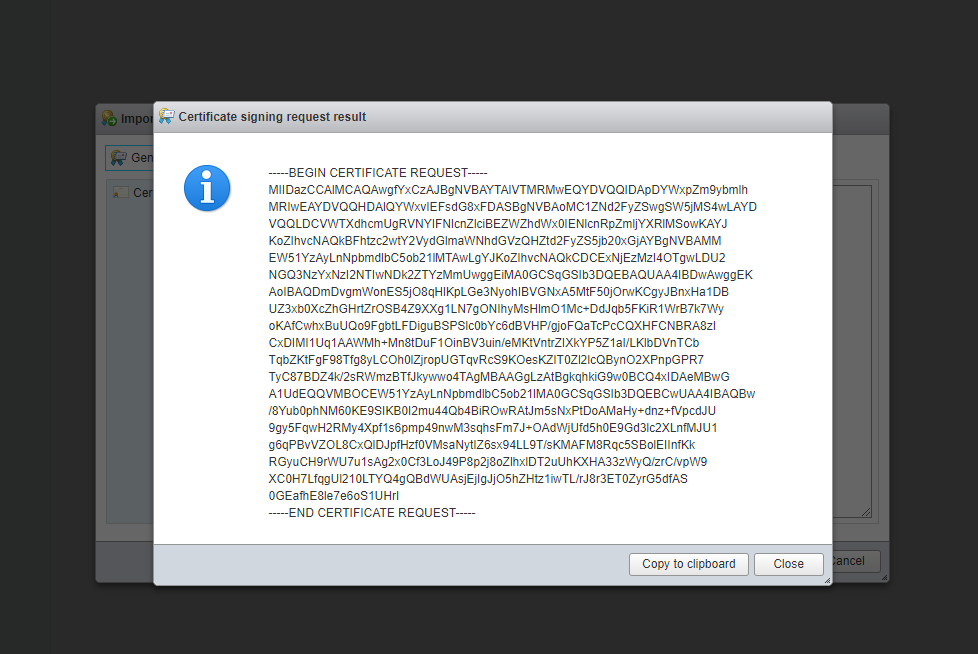
Now store the contents of this request in a file: servercert.csr and issue this command:
openssl ca -config openssl-ca.cnf -policy signing_policy -extensions signing_req -out servercert.pem -infiles servercert.csr
This will give you a servercert.pem file, now only the certificate part of the contents of this file needs to be copied to the import window:
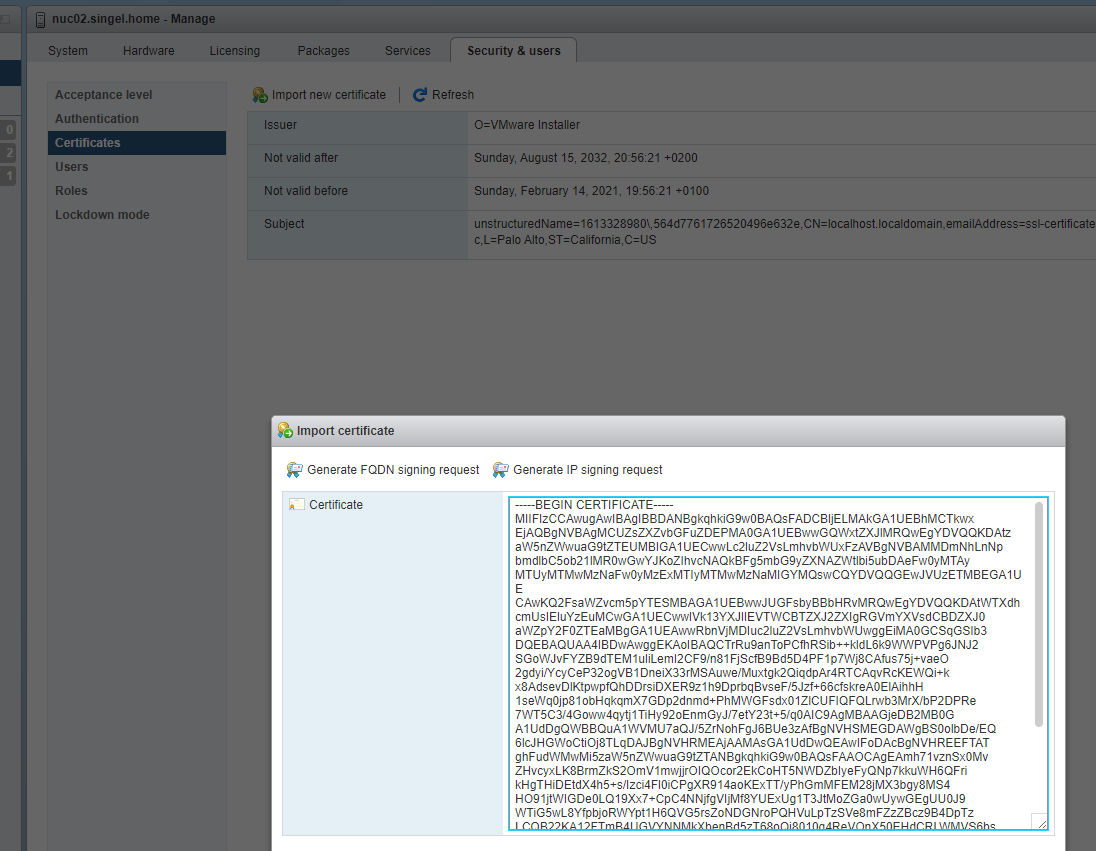
And presto.. done
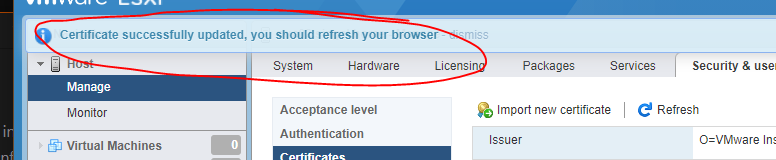
You now should have a valid certificate for your ESXi host.